|
CSI offers comprehensive range of technical and high-value professional
services, including Network Security, Consulting, Network Security
Auditing, Design, Implementation, Maintenance, and Facility Management.
The CSI Services are:
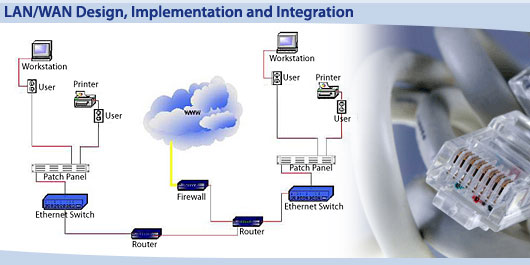
Assessment of Networks
- Identifying critical network applications requirements
- Checking network health and network performance
- Improving and standardizing network documentation
- Developing network management
- Building disaster and business recovery requirements
- Analyzing total cost of ownership and return on investment (ROI)
Network Design
- Deploying and designing proper Active Directory
- Developing proper multi and hybrid network operating systems:
Microsoft, Novell, Unix, Linux, Mac-OS
- Designing multi-routing and multi-switching architecture: multi-protocol
and multi-layered, VLAN schemes, IP addressing schemes
- Designing, developing and deploying strategy on web filtering,
E-Mail filtering, secure connectivity, load balancing, clustering,
fail-over technologies
- Optimizing wireless connectivity, unified messaging: voice,
fax, and email convergence from low-range, mid-range to mainframe
environments
Deployment and Installation
- Implementing and designing systems and network solution
- Upgrading and enhancing the existing systems and network infrastructure
- Licensing, legal and compliance management
Continued Network Services
- Network operating systems, service pack updates, patch management
- Anti-virus analysis and updates
- Upgrades of existing network infrastructure

CSI Process for Network Security Solutions:
Network Security Assessment
- Router, Firewall, IDS, IPS rule-set, and configuration reviews
- Network, server, and infrastructure assessment
- Active and Passive analysis utilizing various scan technologies
- Internal and external testing using various attack techniques
- Authentication, Authorization and Accounting (AAA) review
- Analysis of information security policies and procedures
Computer and System Network Security Design
- Virtual Private Networks, and Remote Access architectures and
topologies
- Intrusion Detection Systems and Intrusion Prevention Systems
- Firewall architectures, DMZ requirements, and redundancy
- Encryption, and Authentication recommendations
- Wireless Security 802.11x, PEAP, EAP
- Mail Cleanser, Content Filtering
- Anti-Virus, Anti-Spy ware
- SAN and IP encryption
Network Security Deployment
- Monitored and Managed Firewalls, IDS, and IPS
- Implementation of designed security solution
- Verification of deployed security solutions
- Operating system hardening
- IOS System hardening
- Patch Management
Continued Network Services
- Routine scans and vulnerabilities
- Log Reviews and GAP Analysis
- IDS, and IPS tweaking
- Patch Updates
- Documentation, and data archival for compliance requirements

IT outsourcing allows the company to take full advantage of communications
services
and technology, freeing one from the operational and support aspects
of information
systems and enabling one company's efforts to be focused on its
core business activities.

We offer a wide range of professional services including consultation
that specialized
in the IT security field. These offers are intended to educate,
to train, to give and to
transform our clients to be more aware of the security aspect, taking
into account
of company infrastructure, culture and budget.
|